Investment Thesis
Cloudflare (NET 0.00%↑) has executed exceptionally well over the last decade and continues to grow revenue in the ~50%/yr range. The company has reinvested every dollar back into the business to grow their edge network, improve their suite of products, and expand into new use-cases and end-markets. R&D and S&M expenses capture most of this investment and EBITDA margins have been <0% as a result. Looking forward, the range of outcomes for both topline growth and EBITDA margins remains extremely wide.
In my opinion, most of Cloudflare’s success emanates from the company’s next-gen software defined network (SDN) and the serverless and V8 Isolate architecture that support it. Matthew Prince, Cloudflare’s CEO and founder, has also built an excellent culture around innovation, executed well on their go-to-market strategy, and has forged plenty of partnerships that have created value for both customers and Cloudflare.
It’s possible that the company continues to lean on these existing advantages and strengths in the future. In a more optimistic scenario, Cloudflare could take significant share in the enterprise market as they continue to innovate, expand product breadth, and provide better quality enterprise products. In addition, Cloudflare could also continue to dominate in the SMB market, where they have ~15-30 free users for every paying customer. Converting some of those free users to paying customers could create a lot of value for Cloudflare. Including all end-markets, Cloudflare currently has ~1.0% market share, and it’s not difficult to see how increased penetration across both enterprise and SMB could take that higher. It’s also possible that Cloudflare’s end-markets grow faster than expected, specifically edge computing which has massive potential and could be a market that Cloudflare and Fastly dominate over the next decade. I expect Cloudflare’s end-markets to grow in the mid-to-high-teens range over the next decade, but it’s quite possible that it’s closer to the low-20% range. All of that said, it’s not difficult to paint a picture where Cloudflare is able to grow revenue at a +40% CAGR over the next decade. Strong top-line growth and high ROI on both S&M and R&D could also lead to EBITDA margins in the 35-40% range, similar to where Akamai is today. In this scenario Cloudflare could be worth >$150/share today.
On the other hand, it’s hard for me to paint a picture where Cloudflare’s competitive advantages are defensible into perpetuity. It’s possible that legacy edge networks like Akamai implement similar network technology, reinvest more in R&D and innovation, refresh their product suite, begin targeting the SMB market, and enter into equally strategic partnerships. Next-gen networks like Fastly could also expand their suite of services and begin to compete more on price, reducing Cloudflare’s ROI on S&M and R&D. At the same time, Cloudflare could struggle with bureaucracy and talent acquisition as they scale, and ROI on R&D and S&M could fall. Cloudflare also operates in an ecosystem where the capital barriers to entry are only moderate - for example, I don’t think it would take a large budget allocation for Google or Microsoft to more aggressively compete in Cloudflare’s sandbox.
In a scenario where YoY growth straight lines from ~50% to 4% over a decade (~25% CAGR), and EBITDA margins increase to ~25% vs. Akamai at ~35% and guidance of ~25%-30%, Cloudflare might be worth ~$20/share. I personally think this is a punitive scenario because it assumes only modest market share gains over the next decade and assumes that ROI on S&M and R&D begins to fall drastically. Given Cloudflare’s success to-date, expansions into new product lines, improving product quality, and massive potential in the edge computing market, I would take the over on these assumptions. All else equal, I’d feel comfortable starting a position in the <$25/share range and would be completely out at ~$100/share. Yes, I know you can fly a 747 through those goal posts, but that’s what happens when the range of outcomes is this wide. I’d also note that since IPO Cloudflare has traded as low as ~$15/share and as high as ~$210/share.
The current price of $60/share sits firmly in my grey zone where I can easily see business performance coming under or over implied expectations. Given the wide range of outcomes (which includes the potential for 65% downside), I don’t view this as a compelling investment today. Said differently, while I love this business, I’ve come to the end of my research without being able to confidently identify any particular reason for why the market has this “wrong”. As an aside, a large part of the learning I did is summarized in the Appendices - so if you’re interested in learning more about the nuts and bolts of what Cloudflare is doing, I’d direct you straight there.
I encourage you to reach out with feedback or comments if you disagree with any of my analysis. I can be reached at the10thmanbb@gmail.com.
Intro
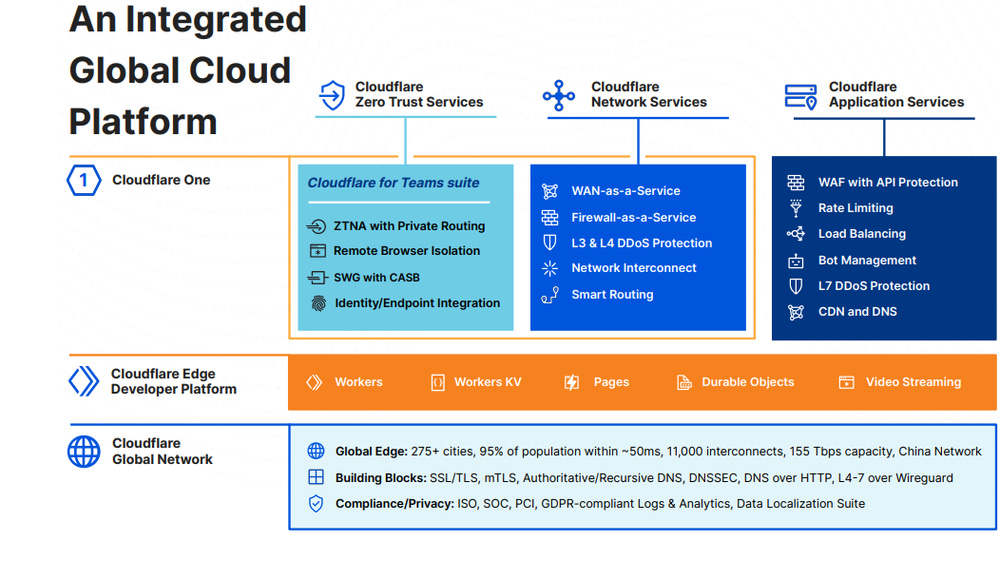
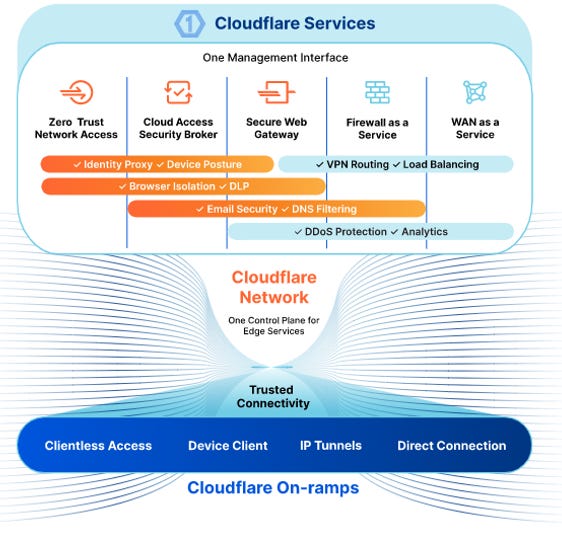
Cloudflare is a global edge network and cloud platform that bundles network services with a wide range of application and security services. The company began as a content delivery provider with a focus on web application firewall (WAF), DDoS protection, and bot management. Eventually Cloudflare expanded into Network-as-a-Service (NaaS) and network security services, bundling the two together into a complete secure access service edge (SASE) service called Cloudflare One. The company also leveraged their network infrastructure to offer edge computing services, which is a small but growing part of their business. See Exhibit A for a broad overview of the company’s full suite of services.
Cloudflare was founded by Matthew Prince, Lee Holloway, and Michelle Zatlyn in 2009. They launched an extremely successful CDN service in 2010 and began building out their network infrastructure to support content delivery and associated services. Although the company is still often referred to as a CDN, I view Cloudflare as an edge network which more broadly captures the full suite of services that they offer today. I’ve included a more detail description of what a CDN and edge network are and how they fit within the internet ecosystem in Appendix A and B.
Cloudflare’s Edge Network
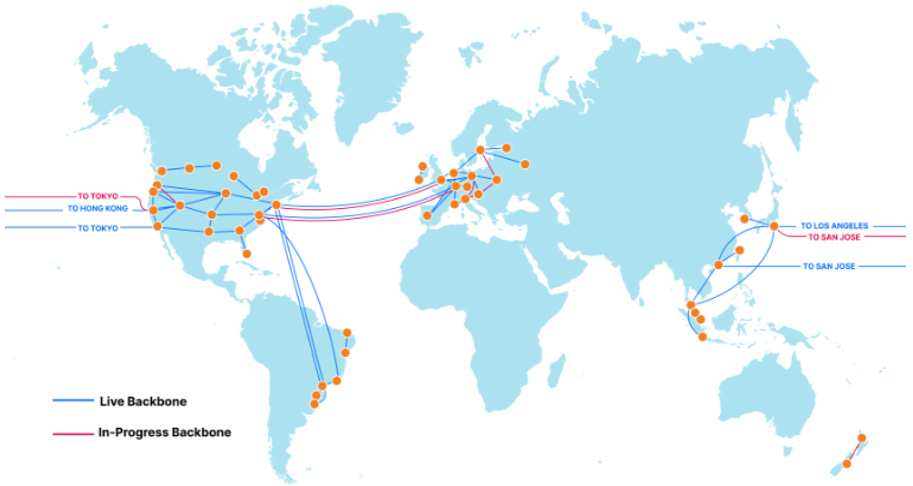
Cloudflare’s edge network is made up of 1,000s of proxy servers located in +270 cities and in +100 countries, connects with over 10,500 networks, and supports +142 Tbps of network capacity. Roughly 95% and 80% of the internet connected world is now within 50 and 20 milliseconds of a Cloudflare point of presence (PoP). See Exhibit B for a map of Cloudflare’s PoPs. Cloudflare’s network has grown at an extremely high rate over the past 5-10 year and continues to expand rapidly. In September 2021 Cloudflare announced an Offices Initiative to expand their PoPs into +1,000 of the world’s busiest office buildings and multi-dwelling units.
The company also began to build its own dedicated global backbone in 2018. This includes dedicated fiber optic cables (rented capacity) and reserved portions of wavelength on long-distance cables with intercontinental and continental connections (including subsea systems), as well as on higher-traffic metro fiber networks. Cloudflare’s backbone provides guaranteed network capacity and consistent latency between various locations, and leads to a more secure, reliable, and efficient network. In some cases (e.g. Chicago to Tokyo) average response time decreased by ~45% (link) after Cloudflare rolled out their own backbone. See Exhibit C for existing and future backbone infrastructure.
Cloudflare’s Services
Customers can join Cloudflare by using a single service, with many free options available to get started, and are able to expand over time by adding on other services as needed. The company’s web dashboard serves as a simple and unified control plane for their deeply integrated suite of services. It’s extremely user friendly and is mostly self-driven. The company offers a handful of standard plans and packages, but also offers a wide range of add-ons and customization. Some of their paid services are offered on a pay-as-you-go basis, while others are offered under annual contract terms.
There are five main categories of services that Cloudflare offers: 1) Applications, which includes content delivery and associated services; 2) Network-as-a-Service; 3) Network security services; 4) Developer services; and 5) Consumer service. I highlight some of Cloudflare’s key services and provide further detail on these in Appendix C. My general takeaways are: Cloudflare’s services are much easier to install, configure, and manage than competitor solutions; Cloudflare offers a wider range and more complete suite of services than most competitors; although Cloudflare’s service may not always rank as best-in-class, they are generally above average in quality and performance vs. alternatives and are priced at or below market average; and the company offers some of the most compelling free services on the market today.
Broadly speaking, Cloudflare offers their customers extremely high ROI services which either significantly reduce a customers costs and/or lead to major network efficiency, performance, and reliability improvements. For example, Cloudflare introduced their Argo Smart Routing technology back in ~2017/2018 that resulted in a 35% decrease in latency, 27% decrease in connection timeouts, a 60% decrease in cache misses, and +50% reduction in bandwidth costs (link). Another example includes Cloudflare’s Zero Trust services that can reduce breach costs by up to 35%, among other benefits (see Exhibit D below). I couldn’t find specific customer payback metrics or ROIs, but Cloudflare’s exceptional growth and market share gains, high dollar-based net retention rates and increasing customer penetration, and customer testimonials would suggest that customers are getting great bang-for-buck.
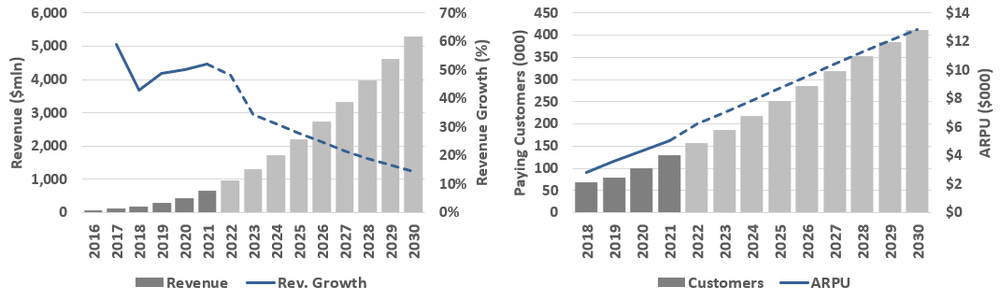
The company has grown revenue at a 51% CAGR between 2016 and 2021, with both customer growth and ARPU growth contributing roughly an equal amount to the topline. See Exhibit E for quarterly revenue between Q1/17 and Q1/22. Cloudflare’s growth in the pre-2017 era was driven almost exclusively from their expansion into the CDN market. However, growth in the more recent years includes their success in entering the NaaS, SASE, and edge computing markets. Unfortunately, Cloudflare doesn’t provide any further revenue breakdown.
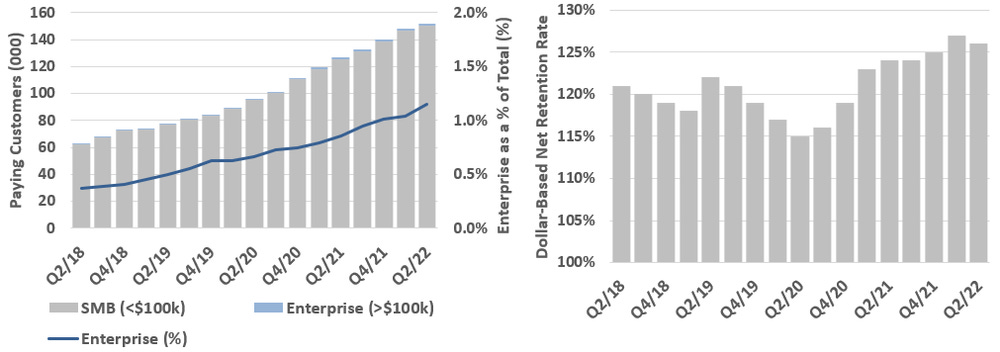
The company continues to grow their share of enterprise customers (>$100k in revenue) which now makes up ~60% of their revenue vs. 21% in 2017. This has been one of the key drivers to overall ARPU growth, and we suspect that the main reason for this is Cloudflare’s expansion into more enterprise tailored products (e.g. NaaS and SASE). However, APRU has also grown from increasing customer penetration from small and medium sized businesses (SMB), which we assume has been in the mid-single digits over the past 5-years. Strong dollar-based net retention rates would also support this; see Exhibit F.
Despite increasing customer penetration, I suspect that Cloudflare’s services continue to make up a very small share of the customer wallet. ARPU for Cloudflare’s enterprise customers is in the $250k-$300k range and in the $2k-$3k range for their SMB customers. Data from Enlyft (link) suggests that Cloudflare’s average SMB customer generates somewhere between $5-$10 mln of revenue. We need to take this data with a large grain of salt, but I think it’s fair to say that Cloudflare’s services cost their SMB customers somewhere in the range of ~10 bps of revenue.
In summary, Cloudflare’s exceptional growth over the past few years can be boiled down to:
Strong value proposition: Low-cost services that improve network costs, efficiency, reliability, and/or overall performance relative to alternative solutions. These services are a small part of the customers overall wallet and have high ROI and short payback periods. Cloudflare is also extremely user friendly and offers a wide range of integrated services making them a more convenient and customizable solution than competitors.
Growing suite of products: Cloudflare’s suite of products has expanded at a faster rate than peers, and the company has leveraged their existing network infrastructure to expand horizontally into other markets. This has driven above average growth in both customer penetration (i.e. ARPU growth) and attracts more customers to the platform by offering a more complete and holistic suite of services.
Cloudflare’s culture, go to market strategy, and inclusive partnerships are a few reasons why the company has executed well to-date and why they have successfully outpaced their peers. However, in my opinion, most of their success emanates from a single competitive advantage: the serverless architecture that supports Cloudflare’s next-gen software defined network (SDN).
Competitive Advantage
In my view, Cloudflare’s next-gen software defined network (SDN) is their main competitive advantage and is where most of the company’s success emanates from. The company implemented a serverless architecture across their network and uses V8 isolates to run applications instead of virtual machines (VMs) or containers. In short, isolates are more efficient for running programs than traditional configurations. See Exhibit G for an example of isolates vs. virtual machines.
This allows Cloudflare to run applications and services on all servers in the network and to assign server capacity on an as needed basis. It makes their network highly programmable and makes it easier to automatically deploy and execute both Cloudflare and customer applications and code; prioritize and optimize performance across the network; role out new products without significant additional operating costs; and has made debugging easier and cheaper. See Appendix D for a more detailed explanation on the differences between V8 isolates vs. VMs and containers.
Other edge networks like Akamai, Limelight, CloudFront, Zscaler, etc. also operate SDNs, but there’s enough evidence to suggest that Cloudflare has taken their serverless technology and architecture to the extreme: Cloudflare has the lowest network costs evidenced by gross margins better than their direct competitors (Exhibit H); allows customers to deploy their solutions unaided with just a few clicks (other competitors require assisted deployment); has managed network fluctuations and traffic much more efficiently (e.g. link); and has been more effective/quicker at integrating emerging technologies and new networking, security, and application capabilities (link). In fact, although it’s difficult to confirm, some sources seem to suggest that Cloudflare is the only edge network that uses V8 isolates (e.g. link). This has been the main driver behind Cloudflare’s high ROI services and above-average innovation velocity, both of which are responsible for the company’s exceptional top-line growth.
That said, despite Cloudflare’s success to-date I only view this advantage as moderately defensible/durable. On one hand, older edge networks like Akamai are burdened with thousands of legacy PoPs and technology. This makes it more difficult and costly to pivot to a new software defined architecture. Cloudflare’s network was built from the ground up and only uses next-generation and high-performance equipment – no legacy hardware – which helps support their SDN and improves efficiency. They also use standard hardware across the entire edge network which makes it much easier for Cloudflare to be hyper-dynamic in how they allocate server capacity and grow the network.
There also exists some moderate barriers to entry. Cloudflare has cumulatively invested >$500 mln and 10+ years into R&D. Any new or existing edge network that implements a next-gen serverless architecture would need to invest a moderate amount in R&D to achieve similar efficiency. As Cloudflare continues to grow and reinvest in R&D, this investment hurdle may become increasingly costly to clear. Edge networks also require a certain degree of scale and connectivity to offer competitive performance. But it’s not primarily an invested capital problem as it is a relationship and connectivity problem. For context, Cloudflare’s net PP&E including right of use assets was ~$340 mln at the end of Q1/22 – I can think of a dozen companies that could outlay that next quarter if it meant guaranteed success in this business. More importantly, it would take a fair amount of time to negotiate with hundreds of ISPs to host edge servers at their IXPs and with the +10,000 other network participates like cloud providers to connect directly to the edge network. It’s also very much a chicken and egg problem – I think this takes scale to work well, but you can’t achieve scale without a competitive service, which requires the capital and time to negotiate with thousands of counterparties to build the network.
On the other hand, companies like Akamai already have sufficient scale, PoPs, connectivity, and a large customer base. They spend more on R&D/year than Cloudflare and can likely replicate most of Cloudflare’s software advantage within a few years of development and implementation and say ~$500 mln of investment. Note that V8 isolate technology is a free and open-source engine developed by Google and is not exclusive to Cloudflare. I expect that many legacy providers will lag Cloudflare in network architecture and technology, but that the gap will quickly close over the next 5-10 years as legacy assets turnover and as the edge network ecosystem continues to expand.
I also believe that there’s not much in the way of stopping any of the large, centralized cloud business like Azure, GCP, or AWS, from entering this market competitively. In fact, most cloud providers offer at least some basic CDN services, with AWS’s CloudFront being the most competitive option out of the three. I have two guesses for why most of these larger centralized cloud businesses haven’t made a major move into this market to date. First, Cloudflare is a third-party network provider and has partnered with all of the centralized cloud providers (excl. AWS) to offer extremely cost-effective solutions. I think it’s more palatable for centralized cloud providers like Azure and GCP to partner with a third-party network provider vs. a direct competitor. This might be why Amazon’s CloudFront has been less successful with connectivity and in providing customers with cost-effective hybrid and multi-cloud solutions. Second, the hyperscale cloud market continues to grow at an exceptional rate. That market has high ROIC and, in my opinion, is a less risky investment for these cloud providers compared to entering into the edge network industry. For example, edge computing could be a massive and profitable market in a decade’s time, but there’s still a wide range of outcomes for market growth and competition. My guess is that the +$1.0 bln and +5 years of R&D required to offer competitive products and start competing with established incumbents like Cloudflare, Fastly, Akamai, and other NaaS and network security participants isn’t a compelling use of capital and resource relative to further investments in their existing cloud business.
Lastly, it's important to highlight that Cloudflare isn’t the only next-gen edge network. Fastly is very similar to Cloudflare in that they also operate a highly efficient next-gen SDN with serverless architecture. The difference between the two is that Fastly has focused much more on speed and computing power at the edge, whereas Cloudflare has focused more on network security. Both edge networks are much more powerful than their peers, but Fastly claims that Lucet (essentially Fastly version of a V8 isolate) is much faster and requires less memory at start up than V8 isolates (link). It’s possible that Fastly strategic approach makes them better situated to handle growth in 5G and edge computing, but I believe the jury is still out on this. Cloudflare had highlighted in a blog post that although speed was an extremely important factor for their serverless Workers platform, consistency, cost, ease of use, and compliance were more important for developers. I don’t have a strong view on whether Fastly or Cloudflare does any of these better than the other, but my general opinion is that the incremental speed with Lucet may not meaningfully set them apart from Cloudflare, at least in the edge computing market. I’ll highlight that Fastly has also performed a bit worse than Cloudflare over the past half decade (Exhibit I), but I think that’s more a consequence of their strategy.
In summary, Cloudflare and Fastly operate more efficient edge networks than their peers. This leads to better performance, lower costs, and a faster rate of innovation. That said, I’m not confident that either will continue to have an edge on software and network architecture a decade from now. I expect the technology gap between legacy edge networks and Cloudflare to close within the next decade, and for CDN, NaaS, and network security services to become increasingly competitive. However, I do expect that Cloudflare will continue taking share in the CDN, NaaS, and network security markets over the medium term. I also expect that Cloudflare’s and Fastly’s next-gen SDN will allow them to dominate the edge computing market over the next 5-10 years, similar to how AWS and Azure are the dominate players in the centralized cloud market. This is already the case and is likely to remain that way over the medium-term (link). I believe that large tech businesses such as centralized cloud providers aren’t likely to meaningfully expand into Cloudflare’s end-markets, although barriers to entry wouldn’t sufficiently deter them if incremental ROIC was compelling enough. In my opinion, this will always be a low-probability but high consequence risk.
Outside of Cloudflare’s more efficient SDN, there are three other unique aspects to the company’s strategy that have contributed to their exceptional growth and success: 1) culture around innovation; 2) go-to-market strategy; and 3) partnerships. I don’t view any of these as durable competitive advantages but believe that they have been crucial ingredients to Cloudflare’s success to-date and will likely support Cloudflare’s future success to some degree going forward.
Strategy
Cloudflare develops and delivers new products and services at a rate many times faster than their competitors. See below Exhibit J for an illustration of Cloudflare’s innovation velocity. For context, Cloudflare expects to have seven “Innovation Weeks” in 2022 where they announce major innovations, new features, and product extensions.
The company’s serverless architecture is certainly a big part of Cloudflare’s ability to innovate: no containers to manage; no scaling to handle; easier to debug, etc. It’s also led to industry leading gross margins, which has allowed the company to reinvest much more of their gross profit into R&D compared to peers (Exhibit K). That said, culture has also been another key driver here. Since the birth of Cloudflare, Matthew Prince has been extremely focused on building a curious and open-minded team for the sake of innovation. For example, 10% of Cloudflare employees are dedicated to an internal organization called ETI (Emerging Technology and Incubations) which has been responsible for over 100 small product releases. Cloudflare is also highly flexible and supportive of small breakout teams and utilizes freemium customers in private beta trials to test, de-bug, and iterate products at a much faster rate than most other development processes. As the company grows, it will become more difficult to maintain a highly innovative team and environment. Bureaucracy creep impacts even the most resilient innovators eventually. However, as long as Matthew Prince remains the CEO I imagine that Cloudflare will find ways to attract and retain creative talent, and will continue to reinvest a significant amount into R&D.
Cloudflare’s go-to-market strategy has also differentiated the company and has been a key driver to gaining market share. The company offers many of their basic services for free, including content delivery services, DDoS protection, SSL capabilities, basic bot management, SSE capabilities for small teams or test trials, and a basic edge computing solution. A handful of other edge networks also offer free services (e.g. Fastly, CloudFront) but Cloudflare seems to offer the most comprehensive and user friendly packages and, on most metrics, has been the most successful with this approach.
This freemium model has been a massive customer acquisition funnel for Cloudflare and has allowed the company to dominate in the entrepreneur and SMB markets. Cloudflare has ~154k paying customers, with only 1% of those (1.5k) paying >$100k/yr (Exhibit L). For context, Fastly and Zscaler had 2.8k and 5.6k customers at the end of 2021, with average ARPUs of $138k and $133k vs. Cloudflare at $5.5k.
There are two reasons why I think Cloudflare’s successful freemium model has set them apart. First, Cloudflare has a massive and untapped customer base. My best guess is that there is anywhere from 2.5 - 5 mln unique customers using Cloudflare today (link), or, put differently, there are anywhere from ~15 – 30 free users for every paying customer. If Cloudflare can successfully monetize even 10% of these users, it would have an extremely large impact to their topline growth over the next decade. It’s difficult to tell how many of these freemium customers could eventually be monetized, but it’s an opportunity that is unique to Cloudflare nonetheless.
Second, free users provide some incremental value to Cloudflare. First, more web traffic on Cloudflare’s platform gives the company more data that they can use to improve services. For example, this helps Cloudflare manage bots, protect against DDoS attacks, and manage other network cybersecurity threats more effectively. Second, beta products are tested on this user base. This is a more cost-effective solution than fully beta testing products internally, but it’s also a more reliable way of finding and solve bugs and therefore improves the paying customer’s experience once the product leaves the Beta stage. Third, this improves Cloudflare’s network utilization, which makes them a more compelling partner for ISPs.
It’s also important to highlight that freemium users don’t add material costs. The company uses spare capacity to service them and they get least privilege access on the network. There’s a risk that freemium users begin to overwhelm Cloudflare’s network, however the company has many levers to pull to avoid this. For example, in a worse case scenario, Cloudflare could begin charging for certain services that could simultaneously push some free users off the platform while converting others to paying customers.
I pulled sales and marketing spend as a percentage of revenue vs. revenue growth for Cloudflare and a select group of their competitors, see Exhibit M. This might not tell the whole story, but it does provide some evidence that Cloudflare’s customer acquisition strategy has worked well to-date.
Finally, it’s worth highlighting that Cloudflare has also done an excellent job at improving their customer experience by partnering with other companies in the ecosystem. Even though other edge networks have also entered into strategic partnerships, I believe that Cloudflare has generally been either the first to create a certain type of partnership and/or created more progressive and inclusive partnerships that drive better value for their customers. One of Cloudflare’s most successful partnerships is their Bandwidth Alliance, which, in my opinion, has given Cloudflare a massive edge over CloudFront. I provide further detail on Cloudflare’s Bandwidth Alliance in Appendix E.
I’m reasonably confident that some competitors will eventually catch up to Cloudflare’s innovation velocity, will expand their target audience to the growing entrepreneur and SMB market, and will enter into equally competitive and valuable partnerships. However, Cloudflare does all three of these things extremely well today and I expect that these will likely continue to support above-average growth and market share gains over the medium term.
Market Share
Cloudflare’s next-gen SDN, innovative culture, go-to-market strategy, and competitive partnerships have all contributed to the company’s edge network expanding at an incredible rate over the past decade. Despite this, the company doesn’t operate the largest edge network today.
It’s difficult to compare Cloudflare to all types of edge networks, but we do have great data on the CDN market. The largest CDN is Akamai which has 2,200+ PoPs and manages somewhere between 20-30% of all website traffic globally (link). Between Grand View Research’s CDN TAM estimate (link) and data from IDC’s annual publication of Worldwide Commercial Content Delivery Network Service Vendor Assessment, we can back into Cloudflare’s CDN market share of ~5%. Exhibit N is from IDC’s annual vendor assessment and illustrates the size of each CDN provider, how each competitor ranks on capabilities and strategy, and how that’s changed over the past three years. Akamai, Cloudflare, CloudFront, and Fastly are all industry leaders.
Despite the company’s mid-single-digit market share, Cloudflare is the most preferred service provider on a number-of-websites basis. Exhibit O shows that Cloudflare is used by 80% of websites that use a reverse proxy service and is used by ~20% of all websites globally (link), which checks out with what Cloudflare’s self-reported market share (link). This compares to Akamai, the largest CDN provider, that only services ~2% of all websites.
The implication here is that the majority of Cloudflare’s customers are either small paying customers or are utilizing Cloudflare’s free services, which checks out with the company’s APRU vs. competitors. As an aside, Akamai’s ~2% share of websites also checks out to me. Akamai provides CDN services to more than half of all Fortune 500 companies: the top 5 global video streaming services, 23/25 top global video game publishers, 8/10 of the largest global banks, etc. Akamai is much more focused on upselling their mega cap customers on security and application solutions vs. attracting new and much smaller customers. For context, Akamai’s revenue from CDN services has only grown at a 2% CAGR over the past 5 years, reaching ~$2.1 bln in 2021. Akamai services are also much more expensive than Cloudflare’s and the company doesn’t offer a free version.
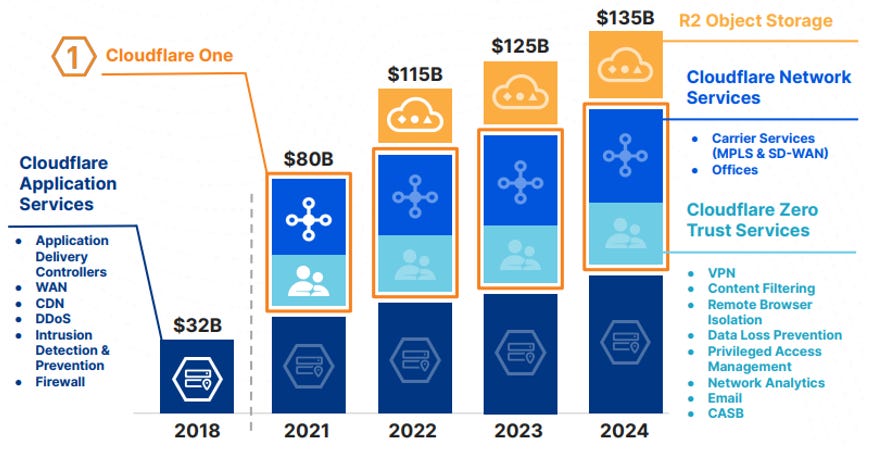
If we expanded our TAM to include other applications and edge networks that provide NaaS and network security services (e.g. Cisco), Cloudflare would rank much lower and would have <1% market share. Cloudflare provides an application services TAM estimate of ~$40 bln, implying that Cloudflare would have <2% share of this market, but if we include the company’s full TAM estimate of ~$115 bln in 2022 (incl. NaaS, zero-trust, and edge computing) we get a market share of ~0.5%.
Although this may make Cloudflare seem like an extremely small competitor, I believe that the company has achieved a significant degree of scale and has sufficient coverage and connectivity to support a wide range of high-performance and competitive services. Cloudflare’s core market remains with the SMB customers today, but there remains a large opportunity for Cloudflare to continue gaining share here as well as further expansion into enterprise solutions and customer base. Even if we assume that Cloudflare’s struggles to gain further market share, the company’s end-markets are growing at above-average rates and should continue to support healthy top-line growth.
Network and Internet Traffic Growth
Cloudflare has achieved a >2x increase in network traffic over the past two years. See Exhibit Q. A big part of this was driven by COVID and the digital sprint to enable work-from-home. Remote work and isolation during COVID also led to an increase in digital consumption for the average person; e.g. more time spent on social media (link). I expect some of this to reverse in ~2022/2023 as some organizations bring their employees back into the office, businesses optimize and improve their hybrid cloud configurations, and as people start looking up from their smart phones. However, there are other very strong secular internet trends and themes that I believe should support extremely high network growth long-term.
For starters, the world is generally becoming more digital as people and businesses get increasingly more utility from digital content, data, and applications. Data creation has grown exponentially over the past two decades and is expected to continue along this trend (see Exhibit R); IDC expects worldwide data creation to grow at a 23% CAGR between 2020 and 2025.
Part of this is driven by increasing internet adoption; internet users have increased by ~1.2x over the past decade, or from 30% to 60% of the worlds population (link). See Exhibit S. Smart phone penetration in developing countries is a big driver here (link), but so is an aging population. Every 18-30 year-old in the U.S. uses the internet today, but only 73% of the +65 year-old demographic are internet users (link). I would expect this trend to continue over the next decade, and for us to eventually see >90% of the world’s population using the internet in the not-to-distant future.
We’re also seeing growth in data consumption per average internet user. A few data points to support this include: GWI’s survey data shows a 13% increase in daily time spent using the internet for global users aged 16 to 64 between 2013 and 2021 (link); the average daily internet time spent on a mobile devices globally increased by 2.8x between 2011 and 2018 (link); and the average size of a web page has >3.0x between 2010 and 2016, driven partly by an increase in images as a % of web page content (link). See Exhibit T for increase in average daily time spent on digital media in the U.S.
Businesses are also becoming more digital and are utilizing the internet and cloud service more as they improve their IT capabilities. Gartner expects global software spending to grow at an 11% CAGR between 2020-2025, with public cloud spending (incl. SaaS, PaaS, IaaS, etc) to go from 33% of overall spend to north of 50%, see Exhibit U. Some of the other industry analysis included in the CTS write-up (link) also suggests that IT spending and digitization are a growing priority for businesses and should support significant internet traffic growth over the next +decade.
Increasing internet users, data consumption per user, and increasing cloud penetration through higher adoption of SaaS, PaaS, IaaS, etc., should all continue to contribute to strong internet traffic growth. On internet flows specifically, the best public data that I could find was from Cisco back in 2017 (link). Cisco expected internet traffic to grow at a 26% CAGR between 2016 and 2021. COVID has obviously accelerated this, but it nonetheless paints a very positive picture.
Lastly, 5G is increasing the amount of bandwidth and traffic that end devices can generate, all while the number of end devices continues to explode. See Exhibit V for 5G capacity vs. previous generations. Edge computing will help IoT devices become smarter and handle more data and will allow edge networks to scale as data processed/generated at the edge grows. It’s still unknown what applications will be run on the edge and how much of the overall load edge computing can take on, but it’s safe to say that it will be significant. Note that if edge networks and edge computing can efficiently handle increased traffic from 5G, then centralized cloud will not necessarily need to scale at the same rate. Edge computing is a small market today but is expected to expand rapidly over the next ~decade along side 5G roll out. For context, only 10% of enterprise-generated data was created and processed outside traditional centralized data center or cloud in 2018; by 2025 Gartner predicts that it will be closer to 75% (link)
All of this should support significant edge network growth. As internet traffic grows, more business will rely on edge network services and existing customers will require more from their network service providers. Cloudflare expects their current addressable TAM to increase by an ~8-10% CAGR in the short-term (2022 to 2024). However, almost all other data points suggest that these estimates are too conservative. For example, the consensus between IDC, Grand View Research (link), and Allied Market Research (link) is for the CDN market to grow at a 15-20% CAGR over the next ~decade, which checks out with the other data points above. The other end-markets that Cloudflare operates in are also expected have explosive growth over the next 5-10 years: MMR (link) and Global Market Insights (link) expect the NaaS market to grow at a 40%-60% CAGR between 2020 and 2027; multiple sources (link, link, link) suggest that the SASE market is expected to grow in the 10%-35% CAGR range between 2022 and 2028; and Grand View Research expects the edge computing market to grow at a 33% CAGR between 2022 and 2030.
In my opinion, growth in these end-markets would suggest that a ~20% revenue CAGR over the next decade is easily in the realm of possibility for Cloudflare. The company will benefit from these strong secular trends but is also likely to continue expanding their TAM by offering additional services (application, security, edge computing, etc.), and taking market share from their competitors. The biggest upside potential for Cloudflare is edge computing, which I believe they are very well positioned to become an industry leader in and will likely become a much larger part of the industry as 5G adoption increases.
Management and Governance
Matthew Prince, Michelle Zatlyn, and Lee Holloway founded Cloudflare in 2009. Lee Holloway was the software architect of the three and was arguably the most crucial of the three to Cloudflare’s early success. Unfortunately, Lee suffered from a severe neurodegenerative disease and left Cloudflare in ~2016 (link). Both Matthew and Michelle remain on as CEO and COO/President, respectively, and have continued to grow the business and execute well.
We have a good gauge on how Matthew views culture, strategy, priorities, and strengths through the many blog publications and presentations that he’s given. I believe that both him and Michelle have been extremely thoughtful on building a culture focused on innovation. As founders, they’ve also grown alongside their customers and are extremely familiar and intimate with their customers needs and wants. Matthew reminds me a bit of Tobi Lutke: both have a knack for identifying extremely obvious problems that their customers face and for finding innovative solutions. Both seem to hold the view that profitability will follow those who successfully make the internet a better place. I believe that Cloudflare’s cofounders have an excellent track record and will continue to lead the company through another decade+ of exceptional growth and success.
Matthew and Michelle collectively own about 12.5% of the economic interest in the business, but control more than half the votes, which is made possible with the dual class ownership structure (Matthew and Michelle own all of the Class B shares, which entitle them them to 10x as many votes as Class A shares). In effect, it’s their world, and shareholders are just living it. That’s not necessarily a bad thing, and I think it’s pretty clear that NEOs are aligned with other shareholders, but the next paragraph highlights some recent controversy on that front.
In December, 2021, Cloudflare granted Co-Founder Performance Awards to Matthew and Michelle. The awards had eight tranches with a 10-year performance period, where each tranche would vest based on a stock price target (ranging from $156-979/share). In theory, Matthew and Michelle could stand to make almost $4.0 billion if every tranche hurdle was met. If the majority of shareholders (excluding the co-founders and a few other interested parties) don’t vote in favor of the awards by December, 2022, then Cloudflare says they will immediately forfeit the program. The Co-Founder Performance Awards were supposed to be voted on as Proposal Four at the last AGM, but Cloudflare pulled the proposal immediately prior to the meeting and two months after getting sued by some shareholders - at this point, I’m not exactly sure if this means it’s dead, or they’re going to find another way to introduce it. In any event, there is a cohort of shareholders that clearly hated this. I don’t think I’m one of them, at least not in the same visceral way (not that I’m a shareholder). The way I see it, what’s 1% dilution if all shareholders generated a 10Y IRR of 22% from the grant date? And at this point, it looks like the awards are getting axed anyway, which I’d take as a positive governance signal - if the people don’t want it, it doesn’t happen. Even without these Co-Founder Performance Awards, Mathew and Michelle own enough equity that I think you can make the argument they’ll strive for some of these objectives anyway (which is why some shareholders were so vocally against the incremental grants).
Lastly, it’s worth highlighting that Cloudflare does fall into the public’s spotlight every so often, both for good and bad reasons. On the positive side, Cloudflare participate in many charitable initiatives, including Project Galileo, Athenian Project, Cloudflare for Campaigns, etc. However, there’s also been several controversies and backlash for providing services to websites with hate speech content, alleged ties to terrorism groups, or other unethical features, content, or organizational ties. Kiwi Farms, an objectively awful website, was the latest of these. Wikipedia provides a list of some of the other controversies (link). Cloudflare also recently published an extremely thoughtful and detailed blog on the company’s stance around content moderation and why this is an extremely complex and challenging discussion and debate (link). In short, I’m not too worried about this. Although Cloudflare, as the infrastructure and security provider, has taken the heat for these one-off issues, (Kiwi Farms, 8chan, etc.), I don’t believe this will materially impact how existing or future customers think about Cloudflare’s services and will have any meaningful impact to their operating metrics.
Valuation
The range of outcomes is extremely wide, and in Cloudflare’s case I don’t have a strong view on what base case assumptions should be. That said, I provide details below on the assumptions and implied valuation that I would feel comfortable taking the over on. I’ve also included sensitivity tables to illustrate how key drivers impact valuation and what assumptions are required to get to the current share price.
Growth
Cloudflare has grown revenue at a 51% CAGR since 2016. What I find impressive is that their YoY growth was relatively unchanged over that period (it didn’t decelerate - granted COVID probably helped). What’s also impressive is that Cloudflare’s growth was driven by a combination of both customer and ARPU expansion. See Exhibit W. It’s difficult to back into Cloudflare’s market share change over this period but Exhibits K, N, and O from above are good indications that the company’s customer and ARPU growth has significantly outpaced peers.
ARPU growth has been driven by both enterprise customers and upselling existing SMB customers and entrepreneurs on the platform. Note that as customer growth decreases, ARPU growth increases, and vice versa. This makes sense given that most new customers likely sign up with Cloudflare’s less expensive package and are a drag on APRU growth. However, this should indicate that older customer cohorts continue to add Cloudflare services at a rate higher than what’s implied by overall ARPU growth. Cloudflare’s reported dollar-based net retention rate (Exhibit X) and cohort revenue data from older investor presentations support this. In my opinion, this is a positive sign that 1) customers stay on the platform and continue to upgrade services over time, and/or 2) that Cloudflare has successfully rolled out new products and features.
Given Cloudflare’s past performance and the macro secular trends highlighted above, I feel comfortable taking the over on a ~25% revenue CAGR between 2021 and 2031. See Exhibit Y for forecasts and key drivers. I assume the number of paying customers triples; ~2/3rds of this comes from monetizing the company’s current freemium users, and ~1/3rd comes from new customers. I also assume that overall ARPU grows at a ~10% CAGR and that the customer split between SMB and enterprises shifts. I assume that the weighted average growth of Cloudflare’s end-markets is somewhere in the ~20% range over the next decade, which implies that Cloudflare continues to take market share, albeit a small amount. I also assume that growth in Cloudflare’s core markets will slow over the next decade, that Cloudflare’s ability to capture market share will erode, and that terminal growth is ~4.5% in 2032+.
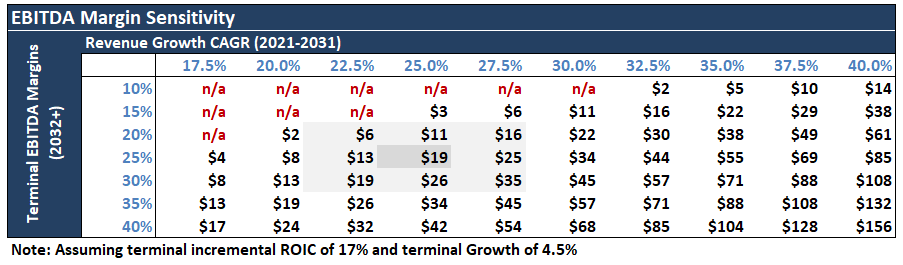
Exhibit Z illustrates my fair value estimate sensitivity to revenue growth assumptions. All else equal, the current price of ~$60 implies +35% growth over the next decade, followed by many decades of above average growth.
Margins
Gross Margins have been consistently in the 84-86% range since 2017, with Adj. EBITDA margins recently coming up into the -10 to 0% range as of ~Q2/20. See Exhibit AA.
Cloudflare’s largest expense has been sales and marketing which accounted for ~44% of revenue on a TTM basis. Roughly 12.5% of S&M has been advertisement spend, which has been relatively constant over the past four years. S&M peaked in H2/19 at ~55% but has been falling ever since.
R&D expense also peaked in H2/19, but hasn’t come down the same way that S&M has. I think this makes sense given that Cloudflare continues to reinvest in their platform; there’s a very large runway for Cloudflare to improve existing products and offer new services and applications. In addition, G&A as a percentage of revenue has been volatile, but the general trend is that this has been falling as Cloudflare scales.
Cloudflare provides “long-term” margin guidance, see below Exhibit AD. Note that Cloudflare’s operating expenses exclude share-based compensation and include D&A. If I add back ~10-15% D&A and subtract off ~5-10% for share based compensation from Cloudflare’s Non-GAAP Operating Margin, I get a long-term EBITDA guidance of ~25%-30%.
I’m comfortable taking the over on ~26% EBITDA margins. I assume that gross margins fall from ~85% in 2021 to 83% by 2031; S&M as a % of revenue falls from ~45% to 28%; R&D falls from ~29% to 18%; and G&A falls from 17% to 13%. For context, Akamai has ~35-40% EBITDA margins today. Exhibit AE provides some comparison of my forward-looking assumptions to current peer metrics. Cloudflare’s EBITDA margins have been negative since 2016, however topline growth has also been consistently in the 50% range. I expect that Cloudflare’s margins will improve as the company matures and growth slows. I assume that S&M expense ~approaches AKAM and LLNW levels of reinvestment but that R&D remains elevated as R&D ROI falls and as Cloudflare continues to improve the platform and maintain their position in industry.
Exhibit AF illustrates my fair value estimate sensitivity to terminal EBITDA margin assumptions.
If I had to guess, I would assume that the current price of ~$60/share is reflecting ~35% growth over the next decade and terminal EBITDA margins of ~30%. These don’t strike me as unreasonable assumptions. However, given the extremely wide variance in outcomes, ~$60/share falls somewhere in the grey area where I have little confidence making a call that this is a great investment idea today. It has been a fun - and painfully long - journey learning about this business, and perhaps I’ll learn something new that will change my mind on the risk/reward at $60/share as I follow this story from the sidelines… but for now this is one for the watchlist.
Appendix A: Content Delivery Network (CDN)
Exhibit A-1 illustrates a very basic and high-level structure of how the internet is configured and provides some context for how content deliver networks (CDNs) and edge networks fit within the internet ecosystem.
Internet service providers (ISPs) in Exhibit A-1 are Tier-2/3 providers. These are the ISPs closest to the end-user - such as individual households and businesses - and charge the customer directly for internet access. These would include companies such as Comcast and Verizon in the U.S., and Bell and Rodgers in Canada. Internet exchange points (IXPs) are the physical locations where ISPs connect and exchange data with other Tier-2/3 ISPs, larger corporate networks, public cloud data centers, and Tier-1 ISPs. IXP’s are co-owned locations where the costs of operating the facility are shared.
Tier-1 ISPs, or transit providers, are ISPs that have global reach. They own and operate major “backbone” internet infrastructure, which includes large terrestrial and sub-sea fiber optic cables. Tier-2/3 ISPs pay transit providers to use their internet backbone infrastructure and to connect to other ISPs around the globe. However, Tier-2/3 ISPs are also able to connect to other neighboring ISPs through peered connections at IXPs. A few examples of transit providers include AT&T, T-Mobile, Verizon, and Tata Communications. Note that many transit providers also own Tier-2/3 networks.
Public cloud service providers such as AWS, Azure, GCP, etc. connect to the internet at IXPs. Larger cloud service providers and corporations also reserve capacity on ISP infrastructure (all tiers) to transfer data more efficiently and reliably between offices, assets, and customers.
Origin servers (or hosting servers) store original digital content and run applications (e.g. websites, SaaS, etc.). These can be owned by the client (on-premise), rented from an off-site third party (cloud servers), or a combination of the two (hybrid cloud). In any case, these servers are typically located very far away from end users, and data from the origin server typically makes multiple hops through the internet to reach end users. For example, let’s say I host this website on my own server in Alaska. If a reader from New York visited my website, data between them and my server would need to travel ~4k miles over internet infrastructure and would include hopping across multiple networks.
This may not seem like a big deal, after all fiber optic cables (the backbone of the internet) send data at literally the speed of light. However, the physical distance that data needs to travel on the internet is one of the largest contributors to latency, and even a small amount of latency can have a large impact on a user’s experience. A few data points to illustrate this point include: 100ms improvement to mobile page loads lifts e-commerce conversion rate by 8.4% (link); 200ms delay can lead to a 4% loss in satisfaction and a 4.3% loss in revenue per visitor (link); a 1 second delay causes a 7% drop in conversion, an 11% drop in page views, and a 16% drop in customer satisfaction (link); latency is a critical element on how Google ranks search results (link).
A content delivery network (CDN) helps solve latency through a geographically distributed group of proxy servers located at the networks edge (a.k.a. edge servers). They do this by caching (a.k.a. storing) digital content sourced from the origin server on the network edge, bringing digital content closer to the end-user. Exhibit A-2 from hhhypergrowth illustrates this.
Going back to the previous example, the first reader form New York to access this web page would be requesting data from my hosting server in Alaska and would likely experience some latency. However, this original request would be managed by the CDN provider who would then store some or all the webpage’s content on their local proxy server in New York. The second person in New York to access this content would then be accessing it from the CDN’s local proxy server rather then from my hosting server in Alaska. Afterwards, if a reader from Miami accessed this webpage, the content would be delivered to the user from the CDN’s New York proxy server vs. the host server in Alaska. The CDN’s Miami proxy server would also cache the webpage data so that additional readers in Miami pull content from the closest proxy server instead of from the New York proxy server or from the hosting server in Alaska. Exhibit A-3 illustrates what this network might look like. Note that the above example illustrates reverse proxy (vs. forward proxy), which is the most common configuration for static content today.
As for where the network edge is physically located, this is unfortunately a bit of a loose term, and the reality is that CDN providers will place servers in many strategic locations called points of presence (PoPs). That said, the most important locations are at IXPs. A CDN partners with an ISP in co-location facilities where the cost of maintaining the physical infrastructure and associated services is shared. An important distinction to make here is that edge proxy servers are generally located much closer to end internet users than the hyperscale data centers owned by companies like Amazon, Microsoft, and Google. My original view was that the large cloud providers like AWS and Azure could leverage their hyperscale datacenter footprints to offer CDN services. However, these hyperscale data centers are massive facilities made up of +5k servers and are typically located “beyond the edge” in locations where land, power, and water are less expensive and easily accessible. As an aside, Azure recently experimented with placing a datacenter at the bottom of the ocean, known as Project Natick, which I though was pretty cool. Proxy servers are much smaller and can be housed at IXPs alongside routers and other network equipment. For context, average latency from a hyperscale facility is 60+ms vs 10-50 ms for servers located on the edge (link), see Exhibit A-4. That’s not to say that these large cloud providers don’t also provide CDN services, but that an effective CDN requires many additional proxy servers located at the networks edge.
And finally, it’s worth mentioning that all CDN’s provide a handful of other benefits and services. I won’t go into too much detail on these but will list some of the major ones out below.
Origin offload. By caching data on proxy servers, CDN’s will dramatically reduce the amount of data that an origin server must provide or handle. This can reduce hosting server costs.
Reducing bandwidth costs. Reducing the average distance and/or amount of data that travels across the internet will reduce infrastructure costs, i.e. data transfer (or bandwidth) costs. This can be anywhere in the +50% cost savings range (link).
Load balancing and reliability. CDN proxy servers are better suited to handle traffic peaks and optimize digital resources vs. hosting servers. Larger CDN’s are also more resilient to hardware failure.
Other performance and security services. Almost all CDN’s provide some form of web application firewall (WAF) services, DDoS mitigation, bot management solutions, and a handful of other and mostly commoditized services like DNS, image optimizations, etc.
Appendix B: Edge Networks
Most companies that offer CDN services like Cloudflare, Fastly, CloudFront, Akamai, etc. have evolved over time and are now leveraging their networks and infrastructure to offer a much wider range of services. Although these companies still compete in the CDN market, and are typically still referred to as CDNs, it’s more appropriate to think about them as edge networks, which is a much broader way of defining what these businesses do today. There are three other major markets that edge networks compete in outside of content delivery and associated services: 1) network-as-a-service (NaaS); 2) network security services; and 3) edge computing.
Network as a Service (NaaS)
Because the internet is not a trusted place, large organizations historically configured their own private WANs to securely connected their multiple offices and assets. This included configuring and running routers and protocols, WAN optimizers, firewalls, DDoS protection, load balancing, etc. Edge networks can use their existing CDN to offer corporations software-defined wide area networks (SD-WANs) as a services (NaaS), relieving them from having to setup and manage their own WANs in-house. By handing these responsibilities off to a third-party, customers save on upfront capital costs (e.g. routing hardware at each location), reduce the amount of time that an internal IT department spends on managing and maintaining the network, and likely results in a more reliable and secure solution with up-to-date technology. Scale, connectivity, and technology (both hardware and software) are the key drivers to having a competitive NaaS offering.
Note that SD-WANS operate on the same infrastructure that supports CDN services but essentially allows customers to build their own private WAN over that network and infrastructure. The difference between CDNs and SD-WANs is that CDNs and associated services are typically designed to help companies deliver the best possible user experience to their customers through the web, and are for all sizes of companies including blogs, small ecommerce businesses, etc. CDN’s sit between a company’s applications (web sites, web apps, mobile apps, etc.) and the users making requests to them. On the other hand, SD-WANs are used by larger businesses with multiple locations to ensure employees get optimal performance when accessing corporate applications and assets across the internet.
Network Security
Similar to how WAF protects web applications, SD-WAN’s also require cyber security solutions. The most comprehensive solution today is a security service edge (SSE) service, which has four key components: 1) zero-trust security (link); 2) cloud secure web gateway (SWG); 3) Cloud access security broker (CASB); and 4) Firewall-as-a-service.
In my opinion, zero-trust security is the most critical component to SSE. Zero-trust is an IT security model that requires strict identity verification regardless of whether the user or device is within or outside a network’s perimeter. This compares to the traditional virtual private network (VPN), or castle-and-moat model, where it’s difficult to obtain access from outside a network but everyone inside the network is trusted by default (Exhibit B-1). Zero trust network access (ZTNA) is the technology that underpins the zero trust security model, but zero trust security is more of a holistic approach to network security and includes many other features like least-privilege access, microsegmentation, multi-factor authentication (MFA), etc.
The zero-trust model was invented in ~2009 (for all intents and purposes here) but didn’t become popular until ~2018, driven in part by increasing adoption of mobile and cloud services. COVID and remote work has propelled the popularity of the zero-trust model, as well as SWG and CASB services, with many enterprises becoming much more eager to implement SSE solutions. Gartner expects that 80% of enterprises will have explicit strategies to adopt SSE by 2025, up from 20% in 2021 and from less than 1% at year-end 2018 (link). Exhibit B-2 shows some of the benefits of using SSE services.
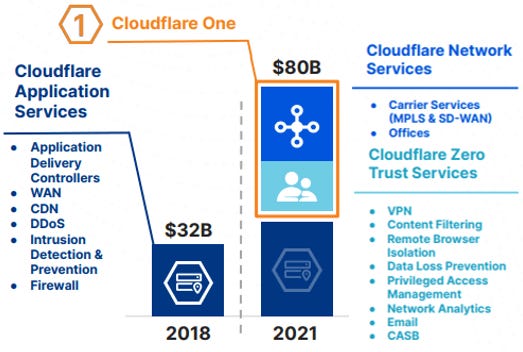
Secure access service edge (SASE) was a term coined by Gartner in 2019 and is a cloud-based IT model that bundles NaaS and SSE services into a single network solution. Many edge networks have either entered this market with their own solutions or are partnering with industry leaders to offer complete SASE solutions. Given the large and growing edge networks that many of these company’s have built over the past few decades to support CDN services, moving into the private network and network security market was a no-brainer. Exhibit B-3 shows the increase in Cloudflare’s TAM by entering these markets.
Edge Computing
Lastly, the other obvious expansion opportunity for these growing edge networks was to introduce programmatic capabilities for customers at their edge servers. This allows customers to run programs and applications at the edge rather than on their own origin servers. Edge computing brings computation much closer to the end-user and can help reduce round-trip time (RTT) over the internet and/or the amount of data that needs to be sent back to origin servers. This can significantly reduce internet infrastructure and origin server hosting costs. Hhhypergrowth provides a great example of how edge computing can parse, sort, and analyze data before sending across the internet, saving the customer on significant data transfer costs:
“…an internet-connected security camera (endpoint) is sending a video feed 24x7 to a centralized data storage & monitoring system in the cloud. Instead of the high cost of having all that continual bandwidth and data storage, edge compute could sit in the middle, and filter the video feed down to only the sections of interest (say, when something is moving in the video feed). It could then make a compute-intensive decision to isolate and extract the 10% of the footage that is relevant, and upload just that portion to the core system, discarding the other 90% of footage where nothing is occurring. This would result in huge savings on the compute & storage costs of the core data systems, as well as the bandwidth into them.”
Edge computing can be thought of as a micro-cloud platform where basic applications can be moved from the origin servers (on-premise or cloud data centers) to edge proxy servers. The difference between the two is that with programmable edge networks and serverless architecture applications can run on any/all servers and are allocated server capacity on an as needed basis. Centralized cloud providers typically ask developers to pick an availability zone and leave it to the customer to manage server capacity requirements.
Note that computing at the edge reduces the computing load on hosting servers but doesn’t necessarily replace the need for a hosting server. For example, businesses may not allow highly sensitive data to be handled on proxy servers, larger computation will still occur at a more capable hosting server, proxy servers aren’t designed to store massive volumes of data which will still take place at larger hosting servers.
Appendix C: Cloudflare’s Services
There are five main categories of services that Cloudflare offers: applications, which includes content delivery and associated services; network as a service; network security services, including zero trust security; developer services; and consumer service. It’s not worth going into detail on each, but I will highlight some of the key features and strengths in the subsections to follow.
Application Services
Application services are broadly split between performance and security and are centered around Cloudflare’s content delivery solution. The free application services that Cloudflare provides include content delivery, unmetered and unlimited distributed denial-of-service (DDoS) mitigation, domain name system (DNS) services, SSL certificates, basic bot management, and a limited number of custom host names for SaaS customers. Other paid-for applications include Argo-Smart routing, load balancing, image optimization (reduces image file size by an average of 35%, link) and resizing, virtual waiting room, automatic platform optimization, video streaming, Web3 Gateways, etc. In my opinion, unmetered and unlimited DDoS protection, bot management, and Cloudflare’s Argo-Smart Routing technology are the company’s best features. Most of these other services are commoditized, although, collectively they help Cloudflare be a fully integrated one stop shop for all their customers needs.
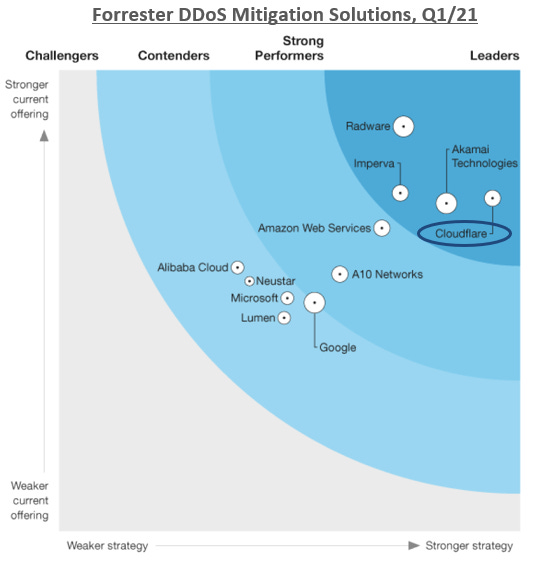
A DDoS attack is a malicious attempt to overwhelm a server with a flood of internet traffic. Network size, efficiency, and mitigation strategies are the key to DDoS protection. Cloudflare relies on a multi-facet approach, but Anycast routing and network diffusion seems to be the company’s main mitigation technique. Given the company’s growing network size and rapidly evolving technology, Cloudflare now offers one of the best DDoS mitigation services on the market. Between 2019-2021 Cloudflare was ranked as an industry leader in DDoS protection by IDC, Gartner, and Forrester. See Exhibit C-1 for Forrester’s DDoS mitigation solution rankings as of Q1/21 (link).
The company continues to set internal records for DDoS mitigation. Cloudflare’s largest mitigated attack occurred in early June 2022, which was a 26 mln request per second attack and was likely equivalent to >1.5 Tbps of traffic. This compares to Cloudflare’s 142 Tbps of network capacity and to one of the largest ever DDoS attacks on record of 2.54 Tbps, which occurred at Google back in 2017 (link). Cloudflare’s recent attack was also targeting a customer that was using Cloudflare’s free plan, which highlights how valuable Cloudflare’s free services can be. Most DDoS attacks are much smaller and easier to manage, and most (if not all) CDN’s can handle the majority of DDoS attacks. However, the frequency and size of DDoS attacks are expected to continue growing rapidly. Cisco expected that the number of DDoS attacks will increase by a 14% CAGR from 2018-2023 (see Exhibit C-2, link), and Polaris Market Research (link) expects the DDoS protection and mitigation TAM to increase at a ~15% CAGR between 2021 and 2030. I believe that Cloudflare’s top-of-class, free, and unmetered/unlimited DDoS mitigation solution is an extremely attractive feature and will continue to set them apart from peers.
Cloudflare also offers basic bot mitigation for free, with more sophisticated bot mitigation solutions and services for higher paying customers. The internet is filled with both good and malicious bots. These are automated applications programmed to do certain tasks. For example, web crawlers (e.g. Googlebots) scan content on webpages to improve search. It’s believed that over 40% of internet traffic is comprised of bot traffic (link) and that a significant portion of this is malicious. However, it’s important to allow good bots access to web properties while simultaneously blocking undesired bot traffic.
Cloudflare uses behavioral analysis and machine learning to identify and accurately classify bots and to detect anomalies on their network. This doesn’t seem to be too dissimilar to other bot-management solutions, although I would make the case that Cloudflare’s software technology is a cut above most of their peers. For example, Cloudflare was a leader in replacing CAPTCHAs. However, in my opinion, Cloudflare’s network efficiency is the key driver that has made them successful with their bot mitigation solutions. Cloudflare handles billions of requests per day over millions of internet properties and is able to leverage this sea of data with extreme efficiency and in real-time to mitigate malicious bots with accuracy and ultra low-latency.
Cloudflare’s full suite of bot mitigation services have made incredible headway over the past two years. Exhibit C-3 shows Forrester’s Bot Management ranking by top industry providers between Q1/20 and Q2/22. As the company’s network grows and as Cloudflare continues to innovate I expect the company to quickly become recognized as a leader in this solution.
It's worth noting that Cloudflare’s web application firewall (WAF) is the cornerstone to Cloudflare’s application security portfolio; it keeps application and APIs secure, thwarts DDoS attacks, manages bots and other malicious activities/anomalies, etc. Forrester’s ranking of Cloudflare’s WAF fell between 2018 and 2020, which isn’t a great look (Exhibit C-4). However, more recent analysis from Frost & Sullivan (link) and Gartner paints a better picture, and given the high velocity of innovation at Cloudflare, the company’s exceptional growth since 2020, and the improvements that Cloudflare’s made on some of their security services (e.g. bot management), I would expect that Cloudflare’s WAF technology would rank much better today.
Lastly, Cloudflare’s best and most differentiating performance application is their Argo Smart Routing technology. Legacy internet routing architecture like BGP and other standard path discovery techniques were designed to optimize for the fewest number of network hops but not for best performing or lowest cost paths (link). As the internet has expanded, this has led to sub-optimal performance and higher than necessary data transfer costs. Argo reduces these infrastructure costs in a few ways.
First, Argo allows Cloudflare to route more internet traffic through their network vs. using more expensive third-party transit, and to optimize routes for performance and costs rather than for the fewest number of network hops. This increases Cloudflare’s network utilization which significantly reduces the per unit costs of transferring data. Cloudflare’s network is extremely well-connected (one of the most peered networks in the world, link), and as the company grows its PoPs, network connections, and backbone capacity, this will only improve.
Second, internet infrastructure is less reliable than I originally thought; cables fail, bogus routes are advertised, routers crash, etc. With Cloudflare’s extensive network, traffic data, and constant machine learning, Argo is able to use real-time data to optimize for the most reliable route. This decreases connection timeouts and improves network efficiency.
And third, Argo has enabled Cloudflare to reroute requests more efficiently to other PoPs on their network in the event of a cache miss. This significantly reduces the load on the origin server by preventing Cloudflare’s PoPs from constantly requesting non-cached content from the origin.
Argo’s beta testing back in ~2017/2018 resulted in a 27% decrease in connection timeouts, a 60% decrease in cache misses, and +50% reduction in bandwidth costs (link). There are also a handful of other benefits to using Argo, for example, it also resulted in a 35% decrease in latency and provides a more secure network connection. Exhibit C-5 illustrates some of these.
Other edge networks would employ similar routing technology, but I suspect that Cloudflare’s Argo solution is better than most given their more next-gen software-defined network and obvious network efficiencies. It's also important to note that Cloudflare’s Argo Smart Routing technology improves network reliability and speed for both content delivery services and for Cloudflare’s SD-WAN solutions.
Cloudflare One
Cloudflare One is the company’s secure access service edge (SASE) solution, which bundles Cloudflare’s NaaS solutions and network security services into a single offering. The company introduced components of this solution prior to 2020, but officially entered the SASE market in Q3/20.
Cloudflare offers NaaS as a separate solution from their full SASE service. Magic WAN is the company’s most inclusive NaaS solution and is designed to completely replace a customer’s legacy WAN architecture and infrastructure. It includes security services like network firewall (Magic Firewall) and DDoS protection (Magic Transit), but both of these services can also be purchased separately. Cloudflare also offers customers the option to privately connect to Cloudflare’s network through their Network Interconnect solution (link), which gives businesses better performance and end-to-end network security.
Like Cloudflare’s network solutions, customers can also use their network security services without having to sign up for the full SASE service. Surprisingly, the company offers basic SSE services for free, including ZTNA, SWB, and CASB.
The company’s a-la-carte network services and network security solutions provide customers with great flexibility and customization. That said, I view these separate solutions as gateways into the full SASE package, which bundles all things network under a single control plane and with customized pricing and features based on the customers needs. Exhibit C-6 gives a good illustration of the entire Cloudflare One solution.
Cloudflare’s SASE service hasn’t yet ranked as an industry leading solution, although it’s only been in the market for less than two years. However, just over 6 months after Cloudflare One was introduced Forrester recognized them as a ZTNA service provider among the top 15, albeit with a less competitive solution than most peers in this group. Gartner also published a secure service edge (SSE is the security component of a SASE solution, link) ranking in Q1/22 and Cloudflare didn’t make this list (Exhibit C-7). The company was also excluded from Gartner’s Q2/21 SD-WAN ranking, which is also not a great look. Note that Cloudflare has continued to add components to their SASE solution since officially entering the market in Q3/20 and has only recently been able to offer what CTO John Graham-Cumming believes is a complete solution. For example, Cloudflare on recently introduced their CASB solution (Q2/22) which is still in a beta version, and which has likely been a drag on Cloudflare’s current ranking with the likes of Gartner.
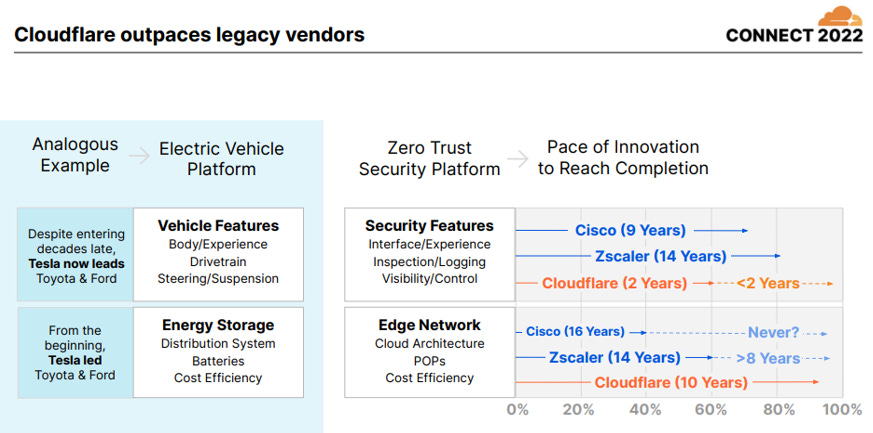
That said, I believe that there’s a good chance Cloudflare One is recognized as a top tier service in just a few more years. Cloudflare was a bit late to the SASE game but still relatively early in the context of the developing market. It took the company only ~2 years to design and develop their solution, showcasing the extremely high velocity of innovation at the company. For context, competitors like Cisco and Zscaler have more than a decade on Cloudflare (Exhibit C-8).
Cloudflare’s distinct advantage over other SASE vendors is their software-defined network architecture and network connectivity. Cloudflare’s private network allows the company to effectively traverse their customers traffic from endpoint-to-endpoint across a more secure and faster network vs. other vendors that rely on the public internet, third-party networks, and/or multiple networks. It’s also enabled the company to integrate new and innovative solutions much more effectively and efficiently than competitors and should allow Cloudflare to stay ahead of the curve as SASE technology continues to evolve. Other benefits of using Cloudflare One include: 1) their unified, consumer friendly, and self-serve control plane make it much easier to implement and manage network services than alternative piece-meal solutions that require more work on the customers behalf and/or white glove support; 2) customers don’t require any additional network hardware.
In summary, I don’t believe that Cloudflare offers top of class service in any individual SASE component quite yet. For example: Fortinet seems to have superior computing power with their proprietary ASIC-powered onsite hardware; Netskope has arguably the most comprehensive secure web gateway (SWG) service; Okta has the moat on identity management (every SASE company needs to partner with Okta), etc. However, Cloudflare now offers a complete and convenient solutions and can likely take the lead in some of these areas as they continue to innovate and take market share. See Exhibit C-9 for Convequity’s view of the SASE ecosystem and where Cloudflare ranks (link, published in Q1/21).
The SASE market is also expected to grow at an extremely high rate, and even if Cloudflare fails to steal market share I believe that they’ll get a piece of this pie and grow ~in-line with industry. Most TAM estimates that I’ve found don’t perfectly reconcile with Cloudflare’s estimate of ~$40-$45 bln, but my main takeaway is that SASE, NaaS, and network security services are expected to grow at a 25%-40% CAGR over the next 6-8 years (e.g. link, link).
Developer Services (Edge Computing)
Cloudflare entered the edge computing market back in 2017 with the introduction of their Workers platform. Like NaaS and network security solutions, this was an obvious evolution for Cloudflare. Similar to how Cloudflare develops and deploys application across their platform and network, customers are now able to do the same and benefit equally from Cloudflare’s SDN and cutting edge serverless architecture. Since the launch of Cloudflare Workers over 450k developers have used the service and have created over 3.5 mln applications. In 2021, 15% of Cloudflare’s paying customers were using their Workers platform.
Cloudflare currently offers three main services for developers through their edge network: Workers, Workers KV, and Cloudflare Pages. Some basic services are free while others are charged based on usage. They also offer add-ons including image resizing, video streaming, and SaaS solutions, with the latter still being tested in a beta trial.
Workers is Cloudflare’s actual application solution. It allows customers to develop applications using JavaScript and to run these applications on the edge. Workers KV is a distributed key-value store that spans Cloudflare’s edge network and is used with Workers for simple data storage & caching. Key-value storage allows applications to leverage off of Cloudflare’s static cache functionality and has expanded the range of use cases and capabilities for Workers. Cloudflare has bundled Workers and Workers KV into a combined solution with basic program and key-value features offered for free. Cloudflare Pages focus on website developers. It’s the developer platform for front-end apps and websites that allow customers to host HTML web pages on Cloudflare’s edge network. Cloudflare Pages is fully integrated with Workers to allow for both static and dynamic website and app content to be collectively hosted on the edge.
In more recent news, and as an extension to Workers KV, Cloudflare has been developing object storage services, called R2, which remains in a closed beta trial today. Key-value storage will continue to be a core part of Cloudflare’s developer services, but there are limitations to this (link, link, link). R2 object storage will allow customers to store arbitrarily large and unstructured data, which take’s Cloudflare’s platform to the next level.
One big advantage that R2 will offer vs. other cloud storage services like Amazons Simple Storage Service (S3) is that it will have zero-cost egress. This doesn’t mean that bandwidth costs will be shifted elsewhere, but that Cloudflare will offer R2 at a fixed price that covers both storage and bandwidth costs. This will be priced on a per/GB and will help developers better forecast storage costs. That said, Cloudflare makes the case that R2’s storage fee will still be lower than many other cloud storage providers given their efficient SDN. Another advantage is that R2 will be managed on a programmable edge network. Reliability is expected to be the same as the other large cloud storage providers, but R2 will have the capabilities to replicated objects and move them into the most optimum locations on their edge network for speed, reliability, and costs.
Both key-value and R2 give developers access to storage for unstructured data like images or webpages. In Q2/22 the company announced D1, their data base solution built on SQLite, i.e. structured data storage (Exhibit C-10). Besides operating on Cloudflare’s network edge, which offers the same benefits the R2 benefits from, I’m not confident that D1 will be a meaningfully differentiate solution vs other data-based service. That said, it was an obvious market and service for Cloudflare to expand into.
Combining Workers with structured and unstructured storage results in a service that directly competes with the large, centralized cloud providers: Cloudflare will be able to run many basic applications on their networks edge. That said, edge networks are only so large and will likely never replace the large Cloud providers. It’s also not yet clear what applications and how much computation can and will be run on the edge vs. centralized cloud.
Lastly, Cloudflare has made significant progress in edge computing and is arguably the lead in this industry. There are many opinions on this, but I think it’s safe to say that Cloudflare and Fastly are positioned well to be the dominant edge computing providers over the short-to-medium term. Exhibit C-11 is Forrester’s edge platform rankings as of Q4/21.
Appendix D: Cloudflare’s SDN & V8 Isolates
The foundation of Cloudflare’s software defined network (SDN) is their serverless architecture, and this architecture is only made possible with Google V8 Isolate technology. The greatest efficiency improvement that isolates offer is the way that memory is managed. It allows Cloudflare’s servers to host many more applications (and/or more advanced algorithms) and significantly reduces the resources each application requires compared to other software architectures (excl. Fastly’s Lucet). Any given isolate can start around a hundred times faster than a node process on a container or virtual machine and consume an order of magnitude less memory on start up. Exhibit D-1 illustrates this well vs. the virtual machine (VM) model which typically has much higher process overhead.
Containers are more efficient than VM, but are less so than isolates because they require the number of containers and allocated server capacity to be determined in advanced, are constantly running even if no one is using the application, and have much longer cold starts (link). Exhibit D-2 illustrates the difference between all three architectures. There are some drawbacks to operating a serverless architecture (for example, isolates provide a larger attack surface than VM, link). However, the improved efficiency, lower cost, and scalability more than offset these.
Appendix E: Bandwidth Alliance
Most public cloud providers don’t charge customers for data ingress, a.k.a. uploading digital content to the cloud. However, when a customer wants to get that data out to their customers, back to their on-premise servers, or to share that data with another cloud provider, they are charged an egress fee (Exhibit E-1).
Egress fees cover the infrastructure cost that cloud providers incur when sending internet traffic over their own global telecommunication backbone or third-party transit providers. This infrastructure can vary from localized connections between routers within the same facility to intercontinental fiber optic backbones. Egress fees are typically calculated on per gigabyte basis and can vary based on the distance that the data needs to travel, e.g. continental vs. intercontinental. See Exhibit E-2 for typical egress fees from the largest cloud providers.
Egress fees are becoming a big problem for customers. As more data and applications are moving to the cloud, it’s becoming extremely difficult for organizations to predict and manage these hidden and growing costs. ZDNet interviewed 300 IT leaders and found that 37% of organizations said that incremental and unpredictable cloud costs are a top concern (link), and respondents in Flexera’s survey self-estimated that ~30% of their cloud spend is unnecessary/waste (link).
Part of the problem is the adoption of multi-cloud strategies, which approximately +80% of enterprises are now embracing (link). As a customer’s IT stack grows and as more data needs to travel between more applications across multiple platforms, the cost of using a hybrid or multi-cloud strategy increases. This becomes a growing cost to the customer and prevents the customer from adopting a multi-cloud strategy and using best in class cloud services (Exhibit E-3). It also makes switching cloud providers more costly and can erode the customers ability to negotiate prices.
In some cases, the high egress fees that public cloud providers charge make sense. Someone needs to cover the cost of the expensive infrastructure that’s required to transfer data around the world. However, legacy internet routing architecture like BGP and other standard path discovery techniques were designed to optimize for the fewest number of network hops but not for best performing or lowest cost paths (link). As the internet has expanded, this has led to sub-optimal performance and higher than necessary data transfer costs.
Cloudflare was able to solve this issue by introducing their Argo Smart Routing technology, with moves data more efficiently and effectively though the internet. However, the other issue that Cloudflare customers were running into was that they were “double paying” for internet infrastructure. As Cloudflare’s network expanded more internet traffic was being carried via Cloudflare’s private network interconnects (PNI) rather than through “middle men” like internet transit providers and ISPs. These PNIs range from short connections between Cloudflare’s and the cloud providers routers (sometimes within the same facility) to Cloudflare’s dedicated capacity on longer haul internet infrastructure. The way I see it is that some of the infrastructure cost was shifting from these “middle men” to Cloudflare, and the customer began to cover these costs through their Cloudflare subscription fees. By paying the same egress fees as a non-Cloudflare customer, Cloudflare subscribers were essentially paying for “middle man” infrastructure costs that was no longer being used.
Cloudflare’s extensive network and Argo technology reduced a cloud customers actual infrastructure costs significantly, but these cost savings weren’t being passed onto the customer. Although Cloudflare offers their customers very competitive rates for using their services, customers were still paying typical egress fees to their cloud providers. By partnering and sharing Cloudflare network data with cloud providers under the Bandwidth Alliance, cloud providers are now able to offer significant discount or no egress fees to customers that don’t incur these “middle man” infrastructure costs to the cloud provider. Almost all the major Cloud providers have joined Cloudflare’s Bandwidth Alliance (Exhibit E-4) with the exception of AWS.
From what I can tell, AWS is currently charging an egregious amount for egress (link) and likely has a significant amount of room to reduce their prices. See Exhibit E-5 for Cloudflare’s estimate of AWS’s mark up. That said, given Cloudflare’s size and network connectivity, Cloudflare and their Bandwidth Alliance are likely more efficient than AWS + CloudFront today and can offer a more cost-effective solution over at least the short-to-medium term. Even if AWS + CloudFront eventually reduced their egress fees, it seems unlikely that CloudFront partners with the other public cloud providers or that AWS partners with Cloudflare. This will make AWS customers stickier, but will perpetually make AWS + CloudFront a less cost-effective solution for multi-cloud strategies.
Other third-party networks like Akamai and Fastly have similar types of partnerships with cloud providers. However, Cloudflare’s Bandwidth Alliance seems to be one of the best and most comprehensive programs to-date. This is likely a function of being the first-mover, driven by Cloudflare’s highly innovative culture, and by having a higher utilized and better-connected network than most of their peers (excluding Akamai).